Emergent organization
From Telecomix Crypto Munitions Bureau
(This chapter needs extensive work)

In order to reason about cooperation and non-cooperation in a crypto-anarchist computer network (which is used by bots and humans to share any form of information with each others), a series of games with different rules can be played out and examined.
Contents |
[edit] Censor-resistant infrastructure
These games are sometimes played by the computer software in order to avoid attacks. For example, the computational resources of one computer is limited and can not be afforded to be spent on cooperating with a denial of service attack: Every agent wish to avoid a successful denial of service attack to be played out against them. Key exchange algorithms such as the Just Fast Keying (JFK) makes sure that the opponent always has the initial computational burden. Put in another way, in order to "play a game" with a computer that is using JFK, one need to cooperate with a key exchange protocol that puts the computational burden on the initator of the connection. This makes it computationally expensive to exploit the key exchange protocol in order to deplete the victims CPU-time (a form of denial of service attack). Computational complexity analysis mixed with game theory results in games that we can study further.
In order to avoid being able of censorship, the nodes can not rely on any single node for organization. Decentralization and distribution of all necessary functions of the network must be built into the communications protocols. Ideally, every node in the network would act in a way that results in that an emergent decentralized and distributed organization of the network is automatically evoked. With distributed hash tables such as Kademlia a sociocyphernetic system can be created (No central node, all nodes are equals. There is no meta-agent.) Optimally the protocol also only uses protocols that does not result in anything but random data being transmitted over the physical networks (internet). I2P does a good job at doing all of this while TOR seems to be slightly less sophisticated (but probably has a more well-examined code). Freenet goes even one step further and describes itself as: "decentralised to make it less vulnerable to attack, and if used in "darknet" mode, where users only connect to their friends, is very difficult to detect." Its almost perfect, if one would not consider how slow it is. At the moment, I2P has syndie which hides the identities of publishers. It also has a torrent client, I2PSnark, that can easily be used to publish information anonymously.
It must be pointed out that this is in no way illegal. It is not illegal to communicate in secrecy with other persons. In order to illegalize a crypto-anarchist network one would have to illegalize the right to communicate anything that the authorities can not understand (random numbers). One can only expect from an ultra-totalitarian regime that one would not be allowed to have private conversations. Despite of this, it is already illegal not to reveal ones cipher keys to the police in a few nations: England, China, North Korea, Burma. In game theory terms, the rules of the protocols needs to be written so that there is no strategy of action that results in any weakness of anonymity for anyone, or damage the network as a whole. The reason is simple: We can not afford to trust the authorities to allow us to have private conversations with each other. The communication networks needs to be operational when authorities tries to silence humanitarian organizations, activists, netizen, lolcat, the bureau director, legion, hierophants, bots, synthetic intelligences, tentacle monsters and troll. We wish to lurk freely in the tubes.
The morality of disobeying leaders that disallows their citizens the right to have private conversations can be debated further. In the process of nullifying surveillance laws by cooperating with others to self-organize a state of crypto-anarchy, we also create possibilities. Censor-resistant infrastructure can be used to undermine corrupt authorities via the act of leaking, or from organization of action related to the authority. This must also be considered when one asks if authorities should be allowed to revoke our right to have private conversations in secrecy. As long as we are able to communicate with each other anonymously, some laws will simply not compute: It is not possible to own anything that can be coded in formal systems -- ideas (patents), memories (copyright) or methods to come to conclusions (patents for algorithms). All information can be modulated into random numbers, and a random number does not have any informative properties. Because of this it is not possible for an authority to see who made what, or if something suspicious even occurs. Thus, agents that does not wish to cooperate with the crypto-anarchist systems are rendered unable to act. Even if one dislikes crypto-anarchism it will be hopefully be ethically difficult to advocate laws that disallows people to have private correspondence with each other.
This is perhaps a battle of applied ethics: Information freedom versus the ideal that some are more fit to power than others. Please also consider this: Authority is like a penis. It's OK to have it. It's fine to be proud of it. But please don't whip it out in public and start waving it around. And PLEASE don't try to shove it down children's throats.
[edit] Games
ALL GAMES HAS BEEN MOVED -- do they fit into this text?
They are useful for describing cybernetic systems, and perhaps the perceived need for cybernetic systems. Maybe they can be useful if one wish to show that centralized command (aka authorities) are not needed. Or that they are even dangerous.
[edit] Intermezzo: Cypherpunk and meta-ideology
RFC2810, Internet Relay Chat: Architecture, is a proposal (or Request For Comments) that defines how IRC servers can cooperate to create real-time communication systems. IRC is one of the oldest forms of direct chat protocols created for the internets and was indeed somewhat of a successor of a protocol for BBS chat. The BBS was typically a computer without internet, people had to phone them with their modems over the Public Telephone Network System. IRC was created 1988, two years before the first web page was created, and three years before the fall of the Soviet Union. In RFC2810 there is a ASCII picture of how an IRC network can look like.
3. Architecture
An IRC network is defined by a group of servers connected to each
other. A single server forms the simplest IRC network.
The only network configuration allowed for IRC servers is that of
a spanning tree where each server acts as a central node for the rest
of the network it sees.
1--\
A D---4
2--/ \ /
B----C
/ \
3 E
Servers: A, B, C, D, E Clients: 1, 2, 3, 4
[ Fig. 1. Sample small IRC network ]
The IRC protocol provides no mean for two clients to directly
communicate. All communication between clients is relayed by the
server(s).
The IRC network organize itself in a tree structure. If cyclic groups appear, such as if D would connect to B, routing of messages becomes difficult. This is a protocol that requires the IRC servers to organize in somewhat star-shaped topologies. This makes it vulnerable to denial of service attacks, or just ordinary failures. While the network is distributed, it is not decentralized. In essence, it kind of reminds us of how the soviet computer network, or the Chilean cybersyn was organized.
Cyberpunk was invented by Bruce Bethke in 1983 and later more-or-less turned into its own literary genre by William Gibson. Lone überhackers lurk the corporate matrix, independently hacking into their mainframes at nights. During the day the cyberpunk either sleep, or lives a miserably life. This literary genre has shaped how media write about hackers. In some sense, it is not possible to be a hacker without at least being associated with the invented cyberpunk lifestyle. But that is besides the point.
The word cyberpunk comes from cybernetics, and punk. Cybernetics is an idea of how one can create complex regulatory systems. It utilizes centralized control, feedback and loopback mechanism from censors. The central nodes in a cybernetic system requires that the sub-nodes below itself in the chain of command reports information back up to the central command. The IRC network is a typical cyberpunk system. IRC is used by hackers (or at least: this is how the media describes it) to organize attacks against the corporate mainframes. In some cases, this is true but very rare. The informal network of Anonymous currently armed with Low Orbit Ion Cannons (LOIC, a DDoS-software) frequently target the corporate websites. Mainframes are out of their reach.
This means that cypherpunks must deal with the art of creating systems which are independent of its subsystems, as the inspection of the function of a subsystem is not possible. Every subsystem is a cyphernetic black box. The first generations of cypherpunk software relied on groups of servers for relaying encrypted e-mail. A user of the system would select a some of the mailservers at random and encrypt their e-mails with all the servers public keys. The mail would then be forwarded between the mailservers, where one cipher after another would be removed from the e-mail, until it was fully deciphered. Once deciphered, the mail could be sent to a mailing list. If private conversation was required, the e-mail could be encrypted with the intended receivers public key. As long as not all the mailservers were owned by the same person, or the owners does not conspire to track the users, its safe to use.
The early dreams of cypherpunks was further expanded with protocols for anonymous banks (Yodelbank was one such bank), which allowed cypherpunks to exchange money without having to pay taxes. A small series of protocols that reinvented the old societies in their cyphernetic forms were created. In the eyes of the first cypherpunks, their systems enabled them to build the perfect anarcho-capitalist worlds inside the computers. Unfortunately for the cypherpunks back in the early 90ies, almost no one understood what they were doing since most ordinary people either did not own any computers, or just played games with them.
The world has since then changed. Today almost everyone owns computer(s) and it does not require any exceptionally educated person to use them. The anonymous banks seems to have difficulties in gaining customers, partly perhaps because it is considered impossible to trust an anonymous stranger with all the money. Alternative decentralized payment systems that does not rely on any single node has emerged and is now being experimented with. BitCoin is one example where agents voluntary engage in agreements of debt directly between each other (in so doing, they create bitcoin currency. No central bank is needed for this.) If agent A owes agent B for something that B created, this debt can be given away to other agents. Since its voluntary and relies on direct trust between agents no banks are required for anonymous money to exist. If anonymous money feels weird, consider that modern money is nothing but numbers inside the corporate mainframes. Going one step further and having the money in your own computer is not impossible.
If there is a distinction between cypherpunk and crypto-anarchism, it lies in the level of abstraction. Crypto-anarchism as such does not deal with money, but the creation of censor-free, decentralized and distributed information infrastructures. This infrastructure can of course be used for any form of communication. The cypherpunk systems are a layer of software and trust built on top of the crypto-anarchist infrastructure. Other forms of "decentralized societies" (an oxymoron?) can of course be built. Crypto-anarchism does not deal with ideologies such as cypherpunk, instead it is a meta-ideology or non-ideology that enables secure implementations of all authority-free ideologies. As our world grows more technically enhanced, the potential for crypto-anarchism grows.
The first generations of crypto-anarchist systems used a few servers to relay their e-mails. While this makes anonymity possible, such systems were slow and were difficult for most humans to use. The old systems did not scale very well either, simply because they were not fully decentralized. It is a bit difficult to create systems that neither relies on a central command nor knows anything about the subsystems that constitutes it.
It is however possible.
[edit] Achieving emergent decentralization and distribution
Wikipedias definition of an emergent algorithm is that it has the following characteristics:
- it achieves predictable global effects
- it does not require global visibility
- it does not assume any kind of centralized control
- it is self-stabilizing
A distributed algorithm is a word that is sometimes used to mean a communication protocol. A distributed hash table (DHT) is a distributed algorithm that decentralize the function of finding a particular agent as well as information stored among the agents.
An ordinary hash table is a data structure that can be used to find stored information within a computer. The amortized time-complexity of a hash table is O(1), meaning that it is as efficient as anything can possibly become. It is often the optimal data structure to store huge amounts of data, but it turns out that its pretty worthless for storing smaller amounts. A DHT is a data structure that is distributed among several computers, and it turns out that most DHTs has complexities of O(Log(N)), where N is the number of nodes in the network.
Since it is a form of distributed database, it requires a distributed algorithm to function. This algorithm can not rely on any central nodes for guidance, since the whole point of the DHT is to be a completely scalable and decentralized structure. One distributed hash table that is of particular interest is Kademlia. The reason is that Kademlia is simple and possible to prove to have a complexity of O(Log(N)).
Remove the description of Kademlia and replace it with the paper. Then add Infiltration, Sibyl and Spartacus below it.
[edit] Addresses
In a Kademlia network, every node selects a random number as its address. If cryptography is used, the address can be the nodes public key. This means that it is not possible to impersonate any other address, unless one successfully cracks the cipher. For simplicity, when explaining Kademlia, we will use 16-bit numbers for addresses. In the paper describing Kademlia, a 160-bit number is used.
An address can thus look like 1011100101010111.
In order to both organize the network of computers and search for information stored in the database, the nodes needs a method to find other nodes quickly. A notion of distance has been introduced to the Kademlia protocol that uses XOR. The distance between two nodes are the first nodes address xor'ed with the second nodes address.
1011100101010111 (Address of node A) xor 0101000101001010 (Address of node B) -------------------- = 1110100000011101 (result)
The result is then interpreted as a number. 11101000000111012 = 5942110. In our example, the distance between A and B is 59421.
[edit] Organization of address space
- Linear (0-65335)
- Think of it as a circle
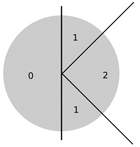
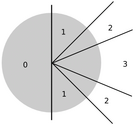
- Explain K-buckets with the circle. Each K-bucket contains a smaller and smaller portion of the address space (exactly half of the previous k-buckets covered address space).
- Explain the Sibyl-attack
- ...
[edit] Protocol
The Kademlia protocol has four RPCs. For each RPC there are two types of messages: Request and answer. Below, requests are to the left. Answers to right.
- PING --
[0|random cookie|#k-buckets]and[0|random cookie|#k-buckets] - STORE --
[1|random cookie|#k-buckets|n-bit blob]and[1|random cookie|#k-buckets] - FIND_NODE --
[2|random cookie|#k-buckets|address]and[2|random cookie|#k-buckets|20 closest addresses] - FIND_VALUE --
[3|random cookie|#k-buckets|address]and[3|random cookie|#k-buckets|n-bit blob]
(maybe i should code this instead of explaining it.)
My proposal to fend of the sibyl attack is: use dynamic k-bucket creation, do not create all of them at the same time. Then let every node have a group of friends that it contact at regular intervals to check how many K-buckets they have. (Alternatively collect statistics about #k-buckets from all nodes -- these numbers should have a very predictable distribution which can be used to compare ones own number of k-buckets against.) Do not allow the number of k-buckets grow larger than the friend with most k-buckets+1. Also, do not accept that the k-bucket with the longest prefix have more nodes in it than the k-bucket with the next largest prefix. Keep track of which nodes has been online the longest time (in a separate hashset) and let them populate the k-buckets when it looks like a sibyl attack is being performed (something which can be detected by comparing the number of k-buckets with ones trusted friends.) As it can be assumed that the friends addresses are randomly (somewhat evenly if there are enough of them) distributed over the address space, the attack should be more difficult to perform. (but not completely impossible.)
- As exponential growth of the number of participating nodes can be assumed (I2P grows exponentially) the number of k-buckets should increase with linear speed.
- Estimating number of participating nodes can be done by measuring how many k-buckets one has. Four buckets = at most 20 + 2*20 + 4*20 + 8*20. Thus, a network with a million nodes should require 9 k-buckets.
- Alternative solution to the attack: Store each blob at two addresses. The hash of the object, and the hash of the hash of the object. If it is not available at the first location, try the 2nd.
- Introduction to Distributed Hash Tables and Kademlia
- DDoS (countermeasures? - pay the price, stay online in order to force them to pay the bandwidth it takes to keep you offline - or else the targets will grow fewer and the network will become vulnerable as the number of nodes shrink ("we are legion"-meme, the force of anarchy lies in number of cooperating agents) - alternatively: freenets darknet mode?)
- Infiltration (Owning the whole chain of onion/garlic-nodes used in a tunnel, countermeasures? - using nodes that are trusted to be friendly)
- The Spartacus attack (why it is not possible in cipherspace - addresses are public cipher keys, thus one needs to crack the cipher in order to inpersonate anyone)
- The Sibyl attack (shitlisting noncooperative nodes, comparing number of used k-buckets with friendly nodes, statistic detection of attack & countermeasures?)
- Conclusions? - avoid non-random structures