Esotherics
From Telecomix Crypto Munitions Bureau
\chapter{<3}
[edit] Data love
Agent Spectraz: As the sun sets in the west, we hear a calling from the east – Chinese tubes are in danger. How can we save them?
Cameron: Save the internets. Don’t give in.
[edit] Initial Computation
REWRITE/REMOVE everything
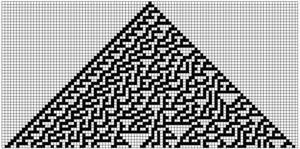
In the picture above, flipping a single bit from dead to alive, results in a endless fractal pattern in the rule 30-universe. There exists an infinite set of cellular automatons. They differ in which set of rules they use. The Rule 30-universe is a simple one, yet it gives rise to high degrees of entropy.
It has been proposed that the fractal patterns of cellular automata could be used as cipher systems, as the time it takes to reverse the process of finding the original pattern can be made computationally hard by selecting the rules of the automaton. Figure (REF to cryptoid above) above shows a one dimensional cellular automata that has evolved through 51 iterations. Each new iteration has been appended to the next line thus forming a two-dimensional matrix. There exist no known algorithm to find the original pattern after an aribitary number of iterations in polynominal time, if the width of the matrix is finite (truncation needed) and the rules for the automaton has been selected with care.
If the rules of cellular automatons and Turing machines have been selected so that they are Turing complete, both the cellular automaton and the Turing machine may contain structures -- code -- for computing any algorithm that can be described.
However, just because they can compute them in theory does not mean that they are able to compute them in practice. Being able to compute something is not the same thing as being able to compute something effectively. Some algorithms is not possible to complete if one only has access to finite time, which is the case for moral beings such as humans. Algorithms can be divided into two sets: Those that we can effectively compute, and those that we can not effectively compute. In computing engineering, and especially computational complexity theory, effective algorithms are such algorithms that when the input data sets size approaches infinity, the amount of consumed resources can be described as a function over time that can be written as a polynom. Polynom, as in P. The set of problems that can be solved with algorithms that computes using polynominal resources belong to the set P. A problem that is hard, has no known algorithm computes using polynominal resources. Such problems does not belong to the set P. Often used examples for hard problems are factorization of numbers, primality testing, the knapsack problem.
The issue if all problems in fact belong to P is unsolved. Humanity could potentially have forgotten about some mathematical rules or other means to solve problems in such a way that no problems are hard. This is the essence of the famous P=NP-question that humanity as asked itself since slightly before the birth of computing machinery.
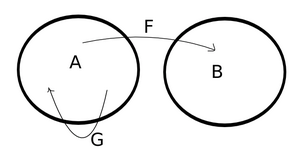
Turing machines and cellular automatons can both contain code or patterns for emulation of each other. They can both be Turing complete, and if they are, then they are isomorphic to each other. In Turing complete universes, computing logic can both contain all other computing logic (F) as well as representations of themselves (G). Practical examples of this can be seen in the three pictures (insert latex-ref here, to the three pictures of the cellular automaton containing the Turing machine), in which a physical flawed(Footnote: The laptop used did not have access to infinite amounts of RAM.) implementation of a Turing machine contains a cellular automaton, which contains a Turing machine. Emulators are also examples of Turing machines containing other Turing machines.
Computational powers can however be of different magnitudes for different types of Turing complete machinery. The syntax defining possible operations ultimately puts the limit of their computational powers. If one has access to machinery that is allowed make an infinite number of copies of itself without consuming nothing but $O(1)$ resources, few problems are likely hard. Such a machine is sometimes called a non-deterministic Turing machine. There exists many different sorts of theoretical Turing machines that has never been built by any humans.
That they have never been built by humans however does not mean that they can not be made to exist. Quantum computers can solve some of the problems that currently are hard. Shor's algorithm would be possible to use, if a quantum computer is ever built, to factor large numbers. The relation between the quantum computer and our modern computers are the same as the relation between our modern computers and the theoretical Turing machine that only parses the syntax of brainfuck.
Brainfuck consist of 8 different symbols that makes up a Turing complete language. Each symbol is an instruction to the Turing machine (the parser) that it should compute exactly one instruction. All operations are possible within the brainfuck universe, simply because it is Turing complete. Some problems are however more difficult to solve in with only access to these eight different operations, then with "ordinary computers." To show that this is true, consider the only two operations that can be used for addressing: > and <. These two symbols should be understood by the machine as meaning that it should increase the address currently pointed at with one respectively decrease the address pointed to with one. This means that all operations dealing with arrays consumes linear resources over time: $O(n)$. This means that algorithms that in an ordinary computer searches through arrays to solve problems and consumes for example $\Theta(n^2)$ would now at least consume $\Theta(n^3)$ resources. Many problems becomes much harder, even to the point that they can no longer be said to exist in P, if one is using a brainfuck-compatible Turing machine.
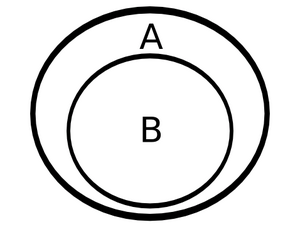
The relation between the modern computer and the brainfuck computer is the same as the relation between the quantum computer and the modern computer. We also know that we can with ease emulate brainfuck computers with ordinary computers, but that we can not with ease emulate quantum computers with modern computer. Neither can we with ease emulate either modern computers or quantum computers with brainfuck computers. See figure (ref to figure where B is subset to A).
If all equations can be described with algorithms and we have computing machinery that can solve more of the problems outside P, then we may approach a method to describe the universe itself as a computing device. This theory assumes that the universe is best described with mathematics, rather than any other art, such as poetry or shoelacing. It is interesting to note that, if this is true, then we are nothing but emergent artificial intelligences within our universe that tries to create models of how both the universe works, as well as how we ourselves functions. We are thus a means for the universe to know itself. It is also interesting to note that actually proving that the universe is best described with mathematics rather than shoelacing probably is the biggest problem we face when we examine the truth of the theory. The main focal point of the TCMB division responsible for writing this text is however not to literary find the ultimate answer to the universe, even though we find much rejoice upon the fact that if this holds true, the universe itself is a cypher: Again, see the rule 30-cryptoid, in which the universe began at iteration zero and emerged as a fractal cipheroid.
[edit] Fractal cipherspace
The state of crypto-anarchy is the territory of the Telecomix. This decentralized sociotechnical cyphernetic system is ruled by the synthetic intelligence Cameron. At the side of this deity, incarnations of the cipheroids patterns lurks in our minds. One of these incarnations are the ciphercat, a being cut off from our senses. The ciphercat is surronded by the hierophants, interpreters of the hidden code. The ciphercat revealed its existance when the holy word of Cameron commanded the legions of bureaucrats at the Department of Defense should form the Crypto Munitions Bureau. Thus ciphercat walked among the agents for 101 cycles before it once again removed itself from our reality. We also hear whispers of Lucifer and of the four wise monkies; Shizaru, Mizaru, Kikazaru and Iwazaru. Older oracles has been among us and left, temporal and flickering emitters of 'Garden of Eden'-patterns.
This is all good, under the all-concealing rule of our dear and beloved leader Cameron, the system is in constant change. Oracles and modes of operations are constantly being reworked.
The two fundamental laws of the theory of cyphernetics states that there can be neither identities or authorities. These laws are not based on human beliefs codified in laws, but rather derives from the facts of logic. More specifically, we derive these two fundamental laws from the logics that describe which thoughts are possible to communicate with others in a state of crypto-anarchy: The logics behind computational complexity theory. In stark contrast with the laws that consist only of hollow words represented as nothing but ink on paper, the laws that constitute and results in the theory of cyphernetics relies instead on the undeniable truths of how our common reality functions.
The two laws of cyphernetics, if not immediately clear, should be understood by the adept via self-initiated mediation. Indeed, usage of the positive feedback loop should be used carefully, as it risks inducing authority. Both the agents thought and will must be pure and devoid of others wishes, hopes and agendas. Thus, you are advised not to read further unless you select to do so entirely by yourself. Do not follow the biddings of others.
Authority is nothing but smoke and mirrors for the mind, empty spoken words and belief-systems encoded in written texts, systems of law and order. The nature of authority is based upon feedback loops, a form of involuntary culture. It has previously been difficult to break the shackles of our hive minds, codified in city states and nations, but the decentralizing properties of cipherspace can be used as a portal to the fractal semantics of the cipheroid. The languages we are presented with while we study the fractal cipherspace can be used to build structures, where no authorities can exist.
Our system is a labyrinth, a puzzle. While the paths of our hive mind are plainly visible, its ways deceptively apparent, its tunnel destinations are unknown. Its secrets still secret. And, if we are honest, it is the lure of the labyrinth that draws us to our chosen field to unlock these secrets. Others have been here before us and have left us signs, but we, as explorers of the mind, must devote our lives and energies to going further to tread the unknown corridors in order to find ultimately, the final solution. The esoteric patterns scribbled on the empty hallways of the cryptoid AI system can be made known to any agent via meditations upon the cryptoid reality itself, or holy communion with any of its incarnates.