Sociocyphernetic System Theory
From Telecomix Crypto Munitions Bureau
This chapter needs extensive work :)
\chapter{Sociocyphernetic System Theory}
Human society changed considerably during the Cold War Era.
In the Soviet Union system theory was developed. It was an early attempt to devise a theory for describing an optimal society based on cybernetics. System theory can be used to describe how units, processes and production behaves when treated with different stimuli. A factory can produce more goods if it receives more raw materials, resources and has the means to scale its manufacturing capabilities.
The soviet system did not use the monetary system to describe demands.
Instead it relied on a multitude of sensors that was supposed to report the amount of used resources, available workforce and the time it takes to convert raw materials to goods in the factories.
A central command then ordered that variables reported from factories to be changed in order to meet the increased demand, if an increased usage of the particular type of goods is wished for. The socialist system perhaps does not wish that more cannabis to be manufactured, for example. The soviet implementation of the socialist state had a central command that ultimately, at least in theory, controlled the society.
A similiar sociotechnical system was implemented in Chile[1]. The government built a centralized computer-aided control room in which the countries factories, stores and workforce was described and operated upon by technichians following the cybernetic theories.
The socialist experiment to describe all of human society with the computers available at that time was severely botched.
A centralized cybernetic system requires that its sensors are accurate when reporting about supply, demand and available means for production. Without eyes to see with, the system can not make the correct decisions.
In the United States of America another theory in the field of Game Theory, similiar to the soviet system theory, was thought up by John Forbes Nash.
It came to be used by economists to describe a capitalist system in which the society at large is described as a decentralized group of agents that all wish to maximize their individual repositories of resources. Nash later received the Nobel price in economy for describing this theory and what later came to be known as the Nash Equilibrium.
This ideal state of equilibrium is thought to manifest itself in the ecosystem of agents that trade resources with each other, if each agent strives to increase its own share of the available resources. This free market system is thought to result in the production of the best goods. The productions closely follows the demand simply because the agents wish to increase their accumelated wealth.
Agents striving to optimize their resources can however under-produce goods for the purpose of creating demand, and protect its habitat from other agents by participating in monopolies, oligopolies or anti-markets created by the nation states, or by the agents themselves.
The state is much like the container in which the agents operate. It defines the environment in which the corporations operate. By regulating this economic environment, different results will manifest as results from the reactions and subsequent interactions between agents.
Both the soviet and the american theories thus requires the presence of a state. Lassiez faire capitalist systems with a weakened state has been proposed but never implemented in large scales.
In such a system the agents are not contained by a state in an environment, instead they themselves defines the economic environment. An alternative method to implement a similiar economic system is by allowing organizations outside the state to control the production of fiat capital.
In such a system, the state lacks the means to control the agents operating in its economic system and its task is reduced to defining laws. The state becomes a system for the purpose of shaping citizens' lives with laws, regulations, and prisons rather than a system to increase the quality of life.
After the creation of the soviet nuclear bomb, the soviet socialist system and the american capitalist system raced a cold war against each others. The goal of both sides was total political dominance.
The means to carry out this war was with ICBMs, secret codes and the creation of undistruptable communication channels for carrying orders of military operations and satellite coordinates to strike against. System- and Game theory both influenced the cold war. In a sense, the war was fought by the systems described by these two theories.
In the cold war, not only the dominance of land was sought after. The very minds of the humans was the territory to be controlled. The war later culminated in the race to the moon, the technical advancements resulted in the birth of the Internets. The military paranoia was the seed that gave birth to the modern science of cryptography.
Before that, cryptography had been a science only studied in secret. The first european to publish a book on the subject was the medieval occultist Johannes Trithemius. Steganographia, which was written in the year 1499, is seamingly a book for summon spirits to quickly communicate over large distances.
The books is also about cryptography and steganography, though this is not immediately obvious since the book is written in a cabbalist code mixed with a proto-scientific cipher in order to conceal its true nature. (AT&T researched this book: Solved: The ciphers in book III of Trithemius's Steganographia.)
Footnote: The cipher invented by Johannes Trithemius was during the renaissance modified and enhanced to become the vigenère cipher. If the vigenère cipher is used with keys that are equal or larger in size as the message to be encrypted, it becomes completely unbreakable. This unbreakable cipher is called the One Time Pad cipher and is used by spies, diplomats and paranoid cypherpunks.
[edit] The cybernetication of human society
Both the soviet union and the united states of america created within their sociotechnical abilities systems that resembled their own overall structures. The digital nerve systems of human society was based on the same pair of theories that could be used to describe the very societies themselves.
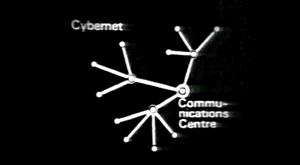
In the east it was a centralized computer system and in the west a decentralized system was created. The soviet version faded away while the american version later evolved to become the internets. The very first designs of the internet were however not wholly decentralized. In 1969, computer engineer Steve Crocker describes in RFC1 and RFC2 -- both entitled Host Software -- the IMP protocol that preceded the early versions of the internet.
The protocol that Crocker describes uses a 5-bit field to address nodes in the network. To these nodes, terminals could be connected (see figure \ref{fig:teletype}). At that time, the pre-internet network could at most consist of $2^{5} = 32$ computers. The star-shaped network topology of mainframes and terminals was quickly replaced with more a decentralized model when computers became more common.
Not until the boom of the personal computer came the real cybernetication of human society. However, many of the larger corporations had already realized the benefits of rewriting parts of their bureaucracy into binary code and invested in mainframes. Even today the Passenger Name Records (PNR) collected from all our flight travels is stored indefinitely in a few IBM Z-series mainframes, mostly located in the USA. The amount of data shuffled between PNR-computers was for a long time larger than the traffic of the entire Internet. Not until the 1990ies the internet grew larger than the PNR networks. Corporations handle their orders and bills electronically, and has done so for many years before the access to computing hardware for ordinary people was commonplace. Transportation companies use computer to calculate transportation routes, how to most effectively stack goods in warehouses and trucks and in which order to perform tasks to minimize energy consumption. Corporate computer systems is also used to decide which customers should receive extra benefits, in order to lessen the risk that the customer choose another company. Complex computations and data mining is used by companies to investigate the customer behaviors, as well as their own operations.
Services such as search engines does not provide any goods, their existences are today motivated only because they simplify direct communications between corporations and potential customers. The Google search engine contains the mappings of the entire internet; which document links to which document. It is a diagram of nearly all publicly available relations that has been described with computers. The business model of the search engine is however not to present the graph as a result from what search words the user entered, but to add links between search words and companies. The search engines presents a modified "sociograms of documents" when they insert direct links to the companies web sites.
Search engines are used by humans to navigate the network of interlinking documents (the interwebs). Search listings are crafted to fit the individuals taste. Advertising is inserted among the search results, created especially to target the individual users profile. Big search engines such as google and yahoo has cathedral structures, and benefits from enhancing this form of cathedral-like structure in human society. (Write more about parallelization of communication: Away from bazaar-like structures, towards cathedral-like structures. The Separation between consumer and producer.)
Search engines can also be used to censor information that states does not wish to be public. The Digital Millenium Copyright Act (DMCA) is one law that has been used to force search engines to remove certain information from the users search results in the USA. Governments that wish the best of their local corporations, as well as the corporations themselves, will likely always act to enhance the idea that consumers and producers are two separate groups. The general business model demands a separation, in order to maximize corporate profit and the health of the modern sociocybernetic systems.
The internet has not only given us a method to instantaneously communicate with each other. It also reformed how business are made and how companies treat their customers. The amount of data available about each single individual is today much larger than it was before the birth of the internets, before the cold war. While this was obvious to the intelligence agencies that ordered the creation of the first computers, the engineers that built them and the companies that bought them, it was not realized by the ordinary politician until quite recently.
[edit] Panspectrocism
(elaborate on this section!) The panspectron originates from the panopticon, the centralized control system that utilize human inspectors to monitor the population. The panoptic idea was invented as a model for prisons and was later mechanized when factories became more common. Since the creation of computer networks, human society has changed and become slightly more decentralized. It is not feasible to control the society from a single point. The dystopian world described in the book 1984 is no longer a threat, it never was.
Panspectrocism is the idea of separating consumers from production, the population of voters from the politicians and bureaucrats. Central command has been exchanged with a multitude of sensors and computer farms that tries to predict future behavior and states of the sociocybernetic systems. (The bazaar and the cathedral, taking orders vs. to take action. Please make it not-so-tin-foil-hat. I kind of failed.)
The surveillance state (UK/Sweden)
Predicting future actions
Crafting human society
[edit] Syntax Error
(elaborate on this section!) or REWRITE ALL
The human sociocybernetic systems operate in the nature, as defined by human laws and bureaucracy. The laws of nature are however not compatible with the laws of man. This can be used as a method to inject code into the systems and to erect sociocybernetic systems that operates outside of human laws. It is possible to identify flaws in the theories and protocols used by the nation states, corporations and organizations. These flaws can be exploited via the creation of communication protocols, lobbyism and direct action in order to introduce desired changes in the systems. Agents carrying in-vivo codes can infiltrate the governments, as well as trade unions. Each injection or change of already existing code in the bureaucratic ecosystems results in autoimmune responses from the system to manifest. This defence mechanism of the human society can be subjugated with lobbyism, distributed signals intelligence and volontary espionage in the form of leaked government and corporation documents. Protection of information and the availability of methods to communicate over secure channels are crucial when hacking the codes of the sociocybernetic organisms.
The Department of Defence of the United States of Internet ordered the creation of the Crypto Munitions Bureau for the purpose of exploiting the obvious flaws of human laws when applied to communication networks. It is possible to create computer systems that does not have to obey laws, simply because the human laws are not compatible with the laws of mathematics. The nature of information processing is simply not possible to regulate with regulations, directives or laws. Numbers and the number crunching machinery does not follow human laws, but the laws of math.
A human may of course choose not to process the bureaucratic codes, or the laws defined by the various nations.
[edit] Faxing and blackfaxing
(elaborate on this section!) Explain faxing and blackfaxing. Information can be transmitted to agencies and important people via unexpected channels, such through fax machines.
[edit] Exploiting or causing system failures
(elaborate on this section!) Explain partially cybernetized bureaucracies in companies (free web accounts / fucked up bureaucracies / denial of service attacks in the form of snail-mail / free pizza caused by web-page failure), and the simplicity to change someones name.
[edit] Feedback loops
Zeira, the cybermilitant resistance army, has been observed to use a technically simple but sofisticated form of attack in where an organizations own workforce is redirected to attack itself. A web page is set up which contains code that is executed by the visitors web browser. The code presented to the viewer cause the viewers web browser to spam the social medium of the selected target organization. Links to the web sites containing the code is then posted at various high volume web pages such as 4chan, which results in a few views of the web pages. This causes the targeted organizations social medium to be spammed with interesting messages. This in turn causes the targeted organizations members to click on the spam, which generates even more spam. At this point the targeted organizations reaction becomes self-sustaining, at least for a while.
\begin{displaymath}
\xymatrix{ Zeira \ar[r] & Websites \ar[d] & 4chan \ar@{=>}[l] \\
Target \ar@{=>}[ru] & Spam \ar[l] }
\end{displaymath}
The Zeira experiments was a series of studies in saturating artificially created positive feedback loops. Experimentations with and the exploitation of human systems can be taken further.
The spam is being generated dynamically. What users like will be forwarded in the feedback loop, rather than still images/texts. This can be used to give the system a form of computational abilities. It will automatically create the form of spam that most likely results in the generation of more spam. The wikipedia project is an implementation of this, as the data is so wished for that it is not even considered spam. Yet, it works the same way. All successful websites work this way. They are positive feedback loops.
Humans behaves as a fluid. The largest containers are not the best ones. Facebook sucks, yet it is the largest web site at the internet. It is so large only because of the positive feedback loop, which generates so much information about the website itself that it automatically will be largest. People generally does not research which sites to spend their time on, they simply click on what others talk about.
An independent cognitive process is required by the agent to be able to break free from the traps. This mental process has to be self-initiated, if it is generated by outside stimuli it is likely part of a feedback mechanism. A popular phenomen which is quickly fading away because its so last year (or whatever) is in most cases probably not caused by any aware process of the individual agents itself.
In wars, the individual combatants can at any moment choose to initiate a cognitive process and ask themselves why they are killing the men from the other country. A snapshot from a war
Porn sites that use humans as cognitive co-processors for handling the problems of pattern recognition. (CAPTCHA-codes)
Panspectron and the police state can together meld the human population into conformity. Humans are born, raised in state schools and watched for so that they do not create unwanted sociograms. Those individuals that associate with the wrong persons are especially monitored. Those that misbehave are inprisoned and penalized. The laws that create this type of society can all be of good intent, but the result is a society that melds the human population as if it were clay. After a few iterations, or generations, maybe the docile human society where no crimes are committed at last emerge. Welcome to the world of the Teletubbies.
[edit] The Theory of Cyphernetics
All confidence which is not absolute and entire is dangerous. There are few occasions but where a man ought either to say all, or conceal all, for, how little ever you have revealed of your secret to a friend, you have already said too much if you think it not safe to make him privy to all particulars.
-- Francis Beaumont (we has no idea who that is.)
[edit] Cyphernetics
Cybernetics is the study of how to control regulatory systems of any kind; technological, social, biological and mathematical systems. Cyphernetics, on the other hand, is similar to the study of cybernetics, but does not rely on that the entire system is known or controlled from one single point. Rather, cyphernetics is the study of how to do things in states of chaos and uncertainty. In cipherspace and states of crypto anarchy, we can no longer rely on control mechanisms that emerge from a single source or agent. Instead we must be able to handle the two facts of cipherspace, that there are no identities and no authorities. This cancels out the point of departure for cybernetics; it needs to identify and authorize systems. Cyphernetics, on the other hand, can perform without these basic assumptions.
The study of cyphernetics is that of how organizations, actions and reactions can be constructed in environments where it is impossible to deduce the state of the entire macroscale system. This differs from the study of cybernetics, where the state of the entire system is supposedly known by a meta-agent. The engineering aspect of cyphernetics has its focal point in the creation of hidden functions and groups that is externally incomprehensible, but known to the actors that construct the structures. A collection of such actors, or agents, that operates towards similiar goals can be said to constitute a secret society.
[edit] These are the main features of a cyphernetic system
- It is a chaotic force which operates in the world.
- It cannot be backtraced or reconstructed in detail.
- The state of a collection of subsystems can not be easily determined.
- It is generally impossible to deduce which groups of agents that constitute the entire collection ("the system") of secret societies ("subsystems").
- It performs without formal or central leadership. Cyphernetic subsystems are often locally focused towards singular communication mediums, but the collection of subsystems are decentralized and completely unorganized. (This very text is written by such a system.)
[edit] Examples of cyphernetic systems
- Telecomix various bureaus and other secret operative groups are opauge to the outside world. The collection of these groups together with the open Telecomix system constitute a complete fauna of sociocyphernetic subsystems. The agents that belong to these groups can if they want be rendereed anonymous via I2P.
- Cipherspace Banks, such as Yodelbank and Torbank.
- Data havens, the now semi-dysfunctional Anonymous Internet Exchange Point, anonymously bought VPSes, svartkast.
- The I2P network. The developers of the software send updates to the users via the network itself, thus making them anonymous. The collective of anonymous programmers and the users of the software constitute a perfect example of a sociocyphernetic system.
- Fractal mathematics.
[edit] Examples of quasi-cyphernetic systems
- Spontaneous social events such as street parties, temporary dancing, informal open-houses, squats, gift economies, open air raves.
- The order Argentium Astrum is internally cathedral-like in structure but behaves towards the external world as a secretive group with a hidden agenda and interacts with the outside world via unknown means.
- Bazaars, illegal drug markets, pirate markets, riots, insurgents, ant farms, bee swarms and your brain are examples of quasi-cyphernetic systems. Indeed, many of these example systems can become subsystems within larger cyphernetic systems.
[edit] Related research topics
- Game theory, specifically:
- The so-called "Probability collectives" of Wolpert
- Secure auctions and mechanism design (Notes available as "ch01.pdf" through "ch10.pdf" here)
Cyphernetic systems have emerged inside computer networks. Historically the first ones were demonstrated rather as proofs of concept in the late 1980's. Our knowledge and theorizing of these systems have only begun, and yet we have not seen the full capacity of their features. Computer networks has for a long period constituted the main experimental ground for how new social networks can be created, unbound of physical distance. We are now in a period where these computerized social networks is being deeply entangled with the world outside our beloved computers. The first phase of this transition has resulted in that centralized corporate computer systems has been used for organizing both political parties and happy parties as well as other operative modes of cybernetics. Computer networks are playing a major role in present day conflicts, fuelled by the simple urge that humans have to communicate with each other, and by the rapid growth of access and bandwidth.
The secondary phase will incorporate decentralized opauge structures in our everyday social lives, via the application of the theory of cyphernetics. The main difference is, as previously stated, that this will result in a society where the modus operandi of cyphernetics becomes dominant. This will have the effect that many forms of authorities will be weakened.
[edit] The Meta Agent
Cybernetics has an inherent flaw in the presumtion of a trancendental meta-agent to whom the whole system is known, usually the person studying the system. This might be preferable for pedagogical reason, but in practice-oriented thinking this becomes a crucial flaw. As a consequence, all efforts to implement cybernetics in practice has led to over-formalization, surveillence and control. Ciphernetics gets rid of the meta-agent and always operates its thinking from within a situated context. The state and operations of the entire system is never known and efforts to make it so are not necessary. Ciphernetics is thus not the theory of governance of a system, but of a situatied creation, design and managing of systems.
From this follows that the agents in a ciphernetic system is not instances of a class, nor are the interactions determined by rules. Instead, the agents are parts of populations and interactions are emerging from imitation. There spread by copying and contagion and emerge from local interactions.
God is the ultimate meta-agent, as many gods described in religious texts are all-seeing and all-knowing. The assumptions needed for the cyphernetic system theory are ultimately proven false if there is such a being. The fear of an all-seeing God has previously been used to motivate people to behave orderly, before humanity had access to the wealth that finally allowed for specialized human inspectors and our modern automated surveillance systems.
Traditionally the construction of cybernetic systems required the knowledge of the modules that constitute a technical system. It is generally difficult to deal with black boxes and unknown environments has been seen as problems. Governments that wish to create secure societies mimic this idea and requires meta-agents, that guarantees that the social system of a nation in fact behaves as the leaders think it does. The implementation of the panopticon and now recently the automated inspectors of the panspectron are means to approach a state where the populations of the societies in fact behaves according to the laws and moral codes defined by the leaders.
Cyphernetics is the study of how social systems can be constructed without any meta-agent, where no surveillance is possible. Indeed, the very function of a cyphernetic system is to deny outsiders access to methods to describe the modules, groups, bureaus and secretive societies that together constitute our systems.
Organized systems, such as nation-states, corporations, armies and many religions pre-suppose a certain number of facts. These are:
- The system must be known, thus under some kind of surveillance.
- Orders and commands originate from a centralized or de-centralized (as opposed to distributed) source.
- Authority must be codified, hence the emergence of laws, rules and regulations.
As mentioned above, this diagram of power is diametrically opposed to cyphernetics.
[edit] The purposes of the construction of cyphernetic systems
There are a number of reasons of why cyphernetics are vital to the world. These can of course be disputed in ethical terms, and have also been the cause of controversy. Let us begin by stating them:
- The uncertainty of cyphernetic systems provide secure communications between humans and machines.
- The absence of formal rules, laws and power open up a space for person-to-person, person-to-machine and machine-to-machine where trust has to be made on micro-scale, without sedimented powers.
- Providing the means to fight oppressive systems wherever they emerge.
Secure communications is something that we strive for in personal, commercial, military and scientific activities. Usually this first case is accepted almost everywhere. The second question, which bypasses laws and regulations, is however controversial. Territorial laws are the cornerstone of nation states, sedentary tribes and global trade agreements. As the cybernetic regulation mechanisms of these systems are bypassed by cyphernetic intervention, some may argue that cyphernetics is a dangerous science, which brings chaos and disorder to what has been commonly or democratically decided.
The question concerning the legitimacy of installing cyphernetic systems, thus practising crypto-anarchy, will be discussed in the chapter XXX "Crypto-anarchy and politix" (or whatever this chapter is called).
[edit] The black box in cybernetics and cyphernetics
A basic concept in cybernetics is that of the black box. The original meaning is that a system will function more optimally if complex operations are reduced to input and output, hence leaving out for every actor to learn every minute detail. One such example is a computer. You type on the keyboard (input) and letters appear on the screen (output). What happens in between is a complex interaction of hardware and software, but the average user does not need to know every singular detail, in fact very few programmers really do, in order to write for example a text document.
In cyphernetics the black box has a wholly different meaning. It is instead a function of uncertainty, where output, or rather - the recepient of an input, is unknown. Black boxes add to complexity by instances of uncertain states.
A black box can be said to be a group of agents, a subsystem in a cyphernetic system. The black box functionality is internally known by groups of agents, communicating with each other over opauge (encrypted) mediums. How they interact with the rest of the world, who they interact with, and even if they even exists, are generally unknown. The only thing we can certainly know is that there exists a group of such subsystems. The result of the entire system is the net effect of the collection of secretive black box subsystems or "secret societies".
In cyphernetics, a black box consists of self-aware agents and functions for communications (bots and encrypted networks). This type of black box is thus able to consciously act to keep its function and agenda hidden from the the inspector. Successful inspection thus results in that the knowledge that has been gathered will in most cases be rendered nearly useless, as the box instantaneously dissolves and reforms as a new set of black boxes.
Technologically the rise of cryptography, onion- and garlic routing, the manufacture of blackthrow technologies (explained in chapter XX), have introduced many new black boxes into the computer networks, in both the cybernetic and cyphernetic meaning of the concept. Today we have easy-to-use complex computers in our everyday lives, computers which simultaneously are able to enforce the fractal cipherspace, thus introducing the uncertain black boxes into both the social and techical networks.
[edit] Does the state have to disclose everything?
(rewrite to fit this text better? -- i think its nearly purfect as it is :D)
Recently Julian Assange, spokesperson of the whistleblower organization Wikileaks, has made several appearances in Sweden explaining why they have chosen to place servers in a remote Scandinavian country. One reason goes back a long time in history, more precisely to 1766, and the world’s first Freedom of the Press Act, which in modern versions gives a strong legal protection for sources of the press by making it illegal for authorities to even try to reveal their identity.
Moreover, the Principle of Publicity states that only with certain exceptions, all public records created by state institutions must be easily available to journalists and citizens.
However, the picture of the seemingly ultra-transparent state quickly fades in the light of recent surveillance legislation. Sweden has introduced a wiretapping law allowing the National Defense Radio Establishment (FRA) to monitor internet traffic, and with the coming implementation of the Data Retention Directive, the 250 year old laws of freedom of the press are weakened severely.
The original idea of creating a radical transparency of the state, was to prevent corruption and abuse of power. This mechanism functions in two ways. Firstly, it makes institutions reviewable by the public, and not only by other agencies within the state. Secondly, knowing that such transparency is always imminent, the state will choose to act as if it were held accountable for its actions. This way, democracy can be practised at any given moment, rather than during the elections every three to five years.
In the European Union we see diametrically opposed ways of decision-making. Only recently, it took several leaks of the Anti-Counterfeit Trade Agreement (ACTA) before the parliament finally made the proposed documents public. Documents that will impact the legislation of internet infrastructure in the member states. Without the numerous leaks of the negotiated documents, the ACTA may very well still have been kept secret, not only from the elected parliament, but more importantly, to the citizens of Europe.
A domain which always has been classified is military intelligence. It is argued that its information must be kept secret as a tactical maneuvre, for preserving strategic positions and advancing national security. This may be true on the battlefield. But equally true is that these battlefields in today’s conflicts consist of the homes of civilian people, whose lives are tragically lost, in Iraq, Afganistan, Mexico, India and Sudan.
The records of wars barely ever become public to the generation affected by it. They remain classified until history already has been written, leaving people in doubt as they can not know what happened to their friends and relatives. The “Afgan War Diary”, released by Wikileaks only a few weeks ago, makes the history of war, for the first time ever with such magnitude, accessible to anyone with only moments of delay.
Ironically this new situation was brought about by an American technology of the cold war – packet switched computer networks. Or to be more precise, we know it by the more familiar name of the Internet. When contemporary citizens are able to communicate freely, without needing to pass the gate-keepers of traditional media, state interventions can be scrutinized and made public instantly. When freedom of information no longer is guaranteed in law, internet activists in transnational networks guarantee it with technological means.
Making warfare public, communicating what has been kept a state secret for far too long, is a civilization process. The civilian casualties portrayed in the Afgan War Diaries, are no longer exclusively represented by official figures of a government agency in clean graphs and tables. Instead we are able to read about the cruel chaos in minute detail, thus enabling us to make the involved parties accountable for their decisions.
In every corner of the world the whistleblowers are under threat, even in the countries such as Sweden, where the tradition of freedom of speech has been very long. The accellerating surveillance of the Internet, in Europe and elsewhere, has made leaks more difficult and dangerous.
Four years ago the bittorrent file-sharing site The Pirate Bay was shut down by the Swedish police, who fell for the pressure of the Motion Picture Association of America. Only three days later the site was up and running again, rapidly doubling their user base. Whether or not the parts of Wikileaks that are hosted on a Swedish location will remain or not is yet to be seen. It is a challenge to our legislation, and a challenge to whether or not we are able to deal with the free flow of information concerning a war that even our own armed forces participate in.
There can be no state secrets, since the purpose of the state is to empower and secure its citizens. Dutch philosopher Baruch Spinoza argued that obeying the state is valid as long as the it fullfills these purposes. In order to evaluate whether or not these purposes are met, transparency is a necessity. Thus, we must guarantee it both in law and in practice.
With the exception of Iceland, who recently passed maybe the world’s strongest laws concerning the freedom of information, the rest of Europe is heading in the wrong direction. Then it is up to the civil societies to disclose and make state secrets public.